Wi-Fi (Wi-Fi) is the most popular, affordable and in-demand technology for data transmission in wireless computer networks. If you have an Internet connection, Wi-Fi technology allows you to distribute Internet traffic among the maximum possible number of users and/or devices. In our article we will look at the most frequently asked questions about Wi-Fi, the Internet and wireless communications.
WiFi in our environment
Why do you need Wi-Fi?
Let's start with a definition. Wi-Fi is a technology for wireless data transmission within a local network, carried out by devices based on the IEEE 802.11 standard. In the current modern world, data transmission technology covers an increasing number of devices: TV, telephone, vacuum cleaner, refrigerator and even a kettle can already use Wi-Fi technology.
Story
Wi-Fi is a wireless network that transmits data on the Internet. The predecessor of Wi-Fi is indeed the radio, and its closest contemporary is Bluetooth technology. Just as in the absence of a radio signal it is impossible to transmit sound, so in the absence of the Internet not a single wireless network will work.
Such networks first began operating in the 1990s. Today they cover the whole world.
Origin of the word
The abbreviation Wi-fi stands for wireless fidelity in English - literally, “wireless precision”. It is understood that thanks to this technology, data is transmitted safely and confidentially from the sender to the recipient.
Pronunciation
The abbreviation is pronounced in Russian as “wi-fi”. Internet users usually have a good sense of humor, so sometimes you can hear fi wi (fi wi) or “wai wah” as a misnomer.
“There is Wi-Fi” - what does it mean?
The expression “there is Wi-Fi” means that in some area (from an apartment to an open field) there is a wireless network to which theoretically you can connect. True, for this it must be open, that is, not password protected.
Radiation harm - truth or myth
Since Wi-Fi works on the same principle as all other waves, there is a belief that radiation from a wireless network is harmful to health. In reality, this radiation is no more harmful than the waves emanating from mobile phones, which we carry with us today. Meanwhile, if you figure out exactly how Wi-Fi works, then these waves will no longer cause fear among users.
How Wi-Fi works and how it works
Basic functions and characteristics of Wi-Fi
Briefly, this technology has two applications:
- Internet connection;
- creating a local network to which additional devices and/or users can connect.
The principle of operation of Wi-Fi, as already mentioned, repeats the transmission of radio waves. In our case, we are talking about transmitting an encrypted signal via microwave (super high frequency) waves over short distances (up to several tens of meters). You need to understand that although wireless networks cover the entire globe, data transmission from Moscow to New York will go through different networks, not just one.
Which Wi-Fi mode to choose
Typically, any device such as a router or modem is set to a mixed mode of use (802.11n/ac mixed or 802.11b/g/n mixed). This is needed to solve problems with connecting devices and increase the chances of compatibility between two devices. This allows you to connect to the router not only from new smartphones, but also from an old laptop.
There is a claim that installing 802.11n (“Only n”) can significantly increase data transfer speeds. This doesn't always work, but you can try. If a person does not have old gadgets that do not support 802.11n, then you can safely install this mode and check the quality of the wireless network and take measurements.
Popular 802.11 bgn set for work
Some routers only operate on the 5 GHz frequency band. It is recommended to set the mixed type “n/ac” for them. You can always check the benefits and changes in speed. It is enough to set a certain mode and take measurements. Then another mode is set. And so on until the optimal one is found. It is important not to forget which settings were changed so that you don’t have to look for them later and reset the router.
Thus, there are many Wi-Fi modes, as well as standards. To choose the protocol to use, you need to determine whether all devices in the house support it. You can read more about the technical part of Wi-Fi on Wiki.
How to connect your device to Wi-Fi
Now let's figure out how to connect various devices to a wireless network.
How to connect wireless Internet on a computer and laptop
To connect to a Wi-Fi network from a computer or laptop, you will need a router. Laptops are usually equipped with a built-in network card, but a computer needs to either upgrade the network card (expensive) or buy a Wi-Fi adapter.
Connection procedure:
- connect the router to the Internet using an Ethernet cable;
- turn on Wi-Fi in the router settings;
- In the Windows taskbar, click on “Wireless Networks”;
- select the network you want to connect to.
- Enter your network password and wait for connection.
You can check such a network and connect in the future by default.
How to use it on a smartphone
In order to connect to Wi-Fi on your smartphone, you need to:
- swipe the screen down (Android) or up (iOS);
- Click on the “Wireless Networks” icon to activate the saved connection.
If you have never connected to such a network before:
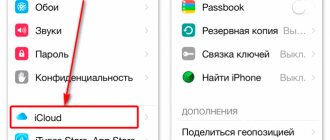
- go to “Settings” and select a Wi-Fi connection;
- in the list of wireless networks, select the one you want to connect to;
- If necessary, if the network is secure, enter the password.
Connection on Android
Be sure to check the option to connect by default if you plan to continue using this network.
What does speed depend on?
The connection speed depends on a number of factors, both on the part of the provider and the user, and on the part of the technology itself. Let's list some of them.
What is WPA?
WPA (Wi-Fi Protected Access) is a protocol that appeared in 2003 and replaced the WEP protocol by the Wi-Fi Alliance. WPA is similar to WEP, but it has improved handling of security keys and user authorization. WEP provides all authorized systems with a single key, while WPA uses the Temporal Key Integrity Protocol (TKIP) to dynamically change the key used by systems. This prevents attackers from creating their own encryption key to match the one used on the protected network. The TKIP encryption standard was subsequently replaced by the Advanced Encryption Standard (AES).
In addition, WPA includes message integrity checking to determine whether data packets have been captured or modified by an attacker. WPA uses 256-bit keys, which is much more secure than the 64 and 128-bit keys used by WEP. However, despite these improvements, vulnerabilities were also discovered in the WPA protocol, leading to the creation of the WPA2 protocol.
The term "WPA key" is sometimes used - this is the password for connecting to a wireless network. You can obtain the WPA password from your network administrator. In some cases, the default WPA password may be printed on the wireless router. If you can't determine your router password, you may need to reset it.
Advantages and disadvantages of Wi-Fi
Like any technology, Wi-Fi has pros and cons.
Pros:
- Wireless network (no tripping over wires);
- Coverage within 70 m is quite sufficient for domestic needs;
- One access point – many devices;
- Higher speed;
- If you connect your smartphone to Wi-Fi, your phone battery will last longer;
- Secure latest protocols.
Minuses:
- Network delays (relevant for gamers);
- Wi-Fi speed limiting – reducing the user’s speed;
- “Natural” signal jamming at home;
- Interference with other devices at 2.4 MHz;
- Poor security of outdated security protocols.
What is WPA2?
The WPA2 protocol appeared in 2004. It is an updated version of WPA. WPA2 is based on the High Security Network (RSN) mechanism and operates in two modes:
- Personal Mode or Shared Key (WPA2-PSK) – uses a shared access password and is typically used on home networks.
- Enterprise mode (WPA2-EAP) – more suitable for corporate networks and commercial use.
Both modes use CCMP, which is based on the Advanced Encryption Standard (AES) algorithm to verify message authenticity and integrity. CCMP is more secure than WPA's original TKIP protocol, making it more difficult for attackers to attack.
However, the WPA2 protocol also has disadvantages. For example, it is vulnerable to key reinstallation attacks (KRACK). Key reinstallation attacks exploit a WPA2 vulnerability to imitate a real network and trick users into connecting to a malicious network instead of the real one. This allows attackers to decrypt small pieces of data that, when combined, can crack the encryption key. However, devices can be patched, so WPA2 is considered more secure than WEP and WPA.
How to set up a Wi-Fi network in your home
A router, or router, is the main way to set up a Wi-Fi network in your home. Below we will consider all aspects of choosing a router and the tasks that it will perform.
Connecting a router
First, the router itself must be connected to the Internet. This is done using special cables that can connect the router not only to a computer or laptop, but to a game console or TV set-top box.
How to log into the router
By logging into the router, you can change the password, network name, configure the router or change its settings. To do this, you need to open a special digital IP address in your computer or phone browser and enter the login and password indicated on the back panel of the router. Often these are addresses 192.168.1.1, or 192.168.0.1 and the matching login and password admin.
Important!
The router login and password are not data for connecting to the Wi-Fi network!
Setting up Wi-Fi the first time you turn it on
When connecting to Wi-Fi for the first time, you must:
- still in the router settings, establish a connection to the Internet using the login and password of the Internet service provider, the type of connection required is PPPoE;
- Next, check the wireless connection option in the router settings;
- set a unique name for your network.
Interesting!
You can leave the network name “MGTS_GPON_5752”, you can rename it “Home”, or you can come up with your own, exotic version.
In the future, the router and all other devices will be connected to this network.
Router indicators - useful information for setup and use
The router has several indicators that convey valuable information about the status of the device and connection:
- PWR (Power) – power – active
- SYS (LOS) – parameters – flashing
- WLAN – Internet (Wi-Fi) – flashing
- LAN 1-4 – network ports – flashing
- WAN (PON) – Internet – blinking
- QSS (WPS) – connection to a Wi-Fi network – active.
To summarize, we can say that if the function is working, the indicator either lights up green or flashes. If the function does not work, the indicator does not blink, or, as in the case of WAN, lights up in orange.
Basic Wi-Fi network settings
Basic wireless network settings include:
- Name ( SSID ) – the simple or unique name mentioned above;
- Security – WPA/WPA2 only;
- PSK password – 8 characters or more;
- Channel – also the above-mentioned 20 MHz or 40 MHz, but in most cases you should specify Auto, and the router itself will select the appropriate channel.
Wi-Fi network protection algorithms
To protect a Wi-Fi network from hacking, there are three main algorithms:
- Configuring the client and access point to use the same SSID, which is not selected by default;
- allowing the access point to communicate only with those clients whose MAC addresses are known to the access point;
- setting up clients for authentication at the access point and traffic encryption.
Most users choose the first option. However, it is worth noting that such precautions are not always advisable and can create additional difficulties when operating a Wi-Fi network. You can read more about protecting wireless networks here.
What is WEP?
Wireless networks transmit data via radio waves, so data can easily be intercepted if security measures are not taken. Introduced in 1997, WEP was the first attempt to secure wireless networks. Its goal was to improve the security of wireless networks by encrypting data. Even if data transmitted over a wireless network was intercepted, it could not be read because it was encrypted. However, systems authorized on the network can recognize and decrypt data because all devices on the network use the same encryption algorithm.
WEP encrypts traffic using a 64-bit or 128-bit hexadecimal key. This is a static key, so all traffic, regardless of device, is encrypted with one key. A WEP key allows computers on the network to exchange encrypted messages, but the contents of the messages are hidden from attackers. This key is used to connect to a wireless network that has security enabled.
One of the main goals of WEP technology is to prevent man-in-the-middle attacks, which it has successfully dealt with for some time. However, despite protocol changes and increases in key size, various shortcomings have been discovered in the WEP standard over time. As computing power has increased, it has become easier for attackers to exploit these flaws. The Wi-Fi Alliance officially abandoned the use of WEP technology in 2004 due to its vulnerabilities. WEP security technology is now considered obsolete, although it is sometimes still used, either because network administrators have not changed the default security protocols of wireless routers, or because the devices are outdated and unable to support new encryption methods. such as WPA.
How to choose a router for Wi-Fi criteria and parameters
Finally, let's look at how to choose a router for Wi-Fi distribution, and what to pay special attention to.
What is a Wi-Fi router and what is it for?
To summarize what has already been said, you need a Wi-Fi router:
- to set up an Internet connection;
- to connect to a wireless network;
- to distribute the Internet to network participants.
Types of routers
Modern routers are divided into different groups according to parameters and functions:
- Wired and wireless;
- Internal or external antenna;
- Supports the latest Wi-Fi standard;
- 3G/4G support;
- Dual-band and tri-band;
- Connection speed: Fast Ethernet, Gigabit Ethernet;
- WAN/LAN ports;
- Additional features: security (WPA2/WPA3), parental controls.
Home router price
Depending on the configuration and functionality, the price of a router starts from 1000 rubles (sometimes lower) and reaches several tens of thousands. However, for home use, the average price ranges from 2,500 to 6,000 rubles, even if users prefer online games.
Huawei WS5200 router
How many antennas do you need?
Typically, a router has either built-in or external antennas. Depending on the model and functionality, there may be one or four. The type and number of antennas improves the quality of the wireless connection, but does not in any way affect the Wi-Fi standard or the amount of Internet traffic according to the tariff plan.
The main difference between routers in terms of antenna type is the following:
- A router with a built-in antenna is more compact, but the signal is also less powerful;
- A router with one or more external antennas transmits a more stable and stronger signal, but requires more space. Sometimes you can connect additional antennas to such a router.
Routers by connection type
Based on the type of connection, routers are divided into wired and wireless.
- Wired routers only have WAN/LAN ports and cannot be used as an access point for a Wi-Fi network. However, wired routers are optimal when there is a heavy load on the Internet, for example, for game consoles and streaming platforms.
- Wireless routers have an antenna that distributes the Internet over a Wi-Fi network. WAN/LAN ports are also present. Such routers are suitable for routine, inexpensive actions, such as transferring photos on the Internet.
Routers by type of ports and connectors
Based on the types of ports and connectors, routers are divided into 5 types:
ADSL routers : receive the signal via telephone cable. They have extremely low data reception and transmission speeds by modern standards.
Ethernet routers : have a WAN port and differ in IEEE protocol. The most common type today.
3 G / 4 G routers : use packet data transfer. The quality of work depends on the coverage provided by the operator.
Routers with connections to PON : an SC optical pigtail is used as a WAN port. Their main drawback is insufficient protection against data interception.
Universal routers : connect several technologies, usually ADSL + Ethernet, or Ethernet + 3G. Also equipped with additional ports and built-in communication modules.
Selecting a Wi-Fi network standard
Today, most routers are designed to work with Wi-Fi 4, Wi-Fi 5 and Wi-Fi 6 standards. When choosing a router model, remember that the standards are backward compatible. In other words, a router with a newer standard (5 or 6) will distribute the Wi-Fi 4 standard, but a Wi-Fi 4 router may not adjust to the newest standard.
What is WPA3?
WPA3 is the third version of the Wi-Fi Protected Access protocol. The Wi-Fi Alliance released WPA3 in 2021. WPA3 provides the following new features for personal and corporate use:
Individual data encryption . When logging into a public network, WPA3 registers a new device in a way that does not involve the use of a shared password. WPA3 uses DPP (Device Provisioning Protocol) for Wi-Fi networks, allowing users to use NFC tags or QR codes to connect devices to the network. Additionally, WPA3 uses GCMP-256 encryption instead of the previously used 128-bit encryption to provide security.
SAE (Simultaneous Authentication of Peers) protocol . This protocol is used to create a secure "handshake" in which a network device connects to a wireless access point and both devices exchange data to verify authentication and connection. Even if the user's password is not strong enough, WPA3 provides a more secure DPP experience for Wi-Fi networks.
Enhanced protection against password guessing attacks . The WPA3 protocol protects against offline password guessing. The user is allowed only one attempt to enter the password. In addition, you must interact directly with the Wi-Fi device: each time you attempt to enter the password, you must be physically present. WPA2 lacks built-in encryption and protection of data on public open networks, making password guessing attacks a serious threat.
Devices using the WPA3 protocol became widely available in 2021. They are backward compatible with devices using the WPA2 protocol.