If you're looking for a good GUI designed directly for the Tor software to connect to the internet anonymously and securely, then you've come to the right place. On our website you have the opportunity to download the latest version of the 2.2.36 Bridge Bundle utility for free in Russian. A link to download the component is already waiting for you at the bottom of this page, but before we get down to business, let’s take a closer look at the functionality of the utility.
Application overview
The program that we will talk about in this review is used to perform anonymous and safe surfing on the Internet. Connection parameters are set by the user through a separate interface, and the work with sites itself is carried out through the Tor application. Let's look at the main features of the tool:
- Connecting to Tor and setting up automatically.
- Disabling and enabling anonymous connections manually.
- Changing your username and other online identity parameters.
- Saving the log of visits and system notifications.
- Entering proxy settings manually.
- Use a password for security.
- Launch the Tor browser automatically.
Some users are faced with a message that Vidalia was unable to connect to the anonymous network. In such a situation, it is recommended to download the component from the official resource. In this case, the latest version of the graphical interface must be used.
Small FAQ
For what? The blocking, which became a reality in January 2016, formally instructs providers to block their users’ access to the Rutracker forum located at https://rutracker.org/. However, some providers went further and accidentally or intentionally blocked or made it difficult to access the tracker servers bt*.rutracker.cc and bt*.t-ru.org. The torrent client, not being able to connect to trackers, does not receive from them a list of addresses of other users participating in a particular distribution. As a result, the exchange speed decreases: it is more difficult for clients to find each other, the breadth of the choice of peers is narrowed for each of them, and it is difficult to find new, yet unknown to the client, distributions. As you know, a thousand peers downloading from each other are much more efficient than ten, even with 100% of the distribution data.
Should I do this? The described steps to bypass blocking are needed only for those whose provider blocks access to tracker servers. The rest should not constantly use the described technique. Keep it for the future as a backup option in case stricter lockdowns are introduced. Also read the section Does your ISP block access to trackers?
Don't torrent over Tor! A famous phrase repeated by Tor developers. The Tor network was not designed to transmit data in such a mode and in such volumes as torrent networks operate. The first and most important reason for this, although not important for us now, is that torrents do not provide anonymity for the participant in the distribution - remember that when it comes to bypassing blocking, we do not strive for anonymity, at least for now. We need to know that by running all your torrents through the Tor network, you will not only reduce its throughput and harm other users, but also significantly reduce your own download and upload speeds. Here we will configure our client so that the Thor network is used only for communication with trackers, and the exchange of distribution data itself will work directly.
Attention! When using this bypass method, your distribution statistics will be partially taken into account or will not be taken into account at all. This is due to the fact that we use the Torus network, and to the peculiarities of recording statistics by our trackers. Below we will give recommendations on how to reduce this effect, but those who are interested in the truthful numbers of distributed gigabytes in their profile should keep this in mind.
Operating instructions
In the form of a short instruction, we will consider how to correctly download and install the software described in the article on a computer or laptop.
Download the program
At the bottom of the page there is a “Download” section. It contains a link, by clicking on which you will receive an archive with the application. We unpack the archive, and then follow a series of simple steps:
- We start the installation of the utility by double-left clicking on the installation file.
- Select the Tor browser in the window that appears using the “Vidalia” add-on.
- At the next stage, we change the program installation path, if necessary.
- We wait for the file unpacking process to complete and close the installer after it is finished.
If the device already has the required version of the browser, then the download option can be removed when installing the software.
How to use
It's time to figure out how to use the browser-based GUI on your computer or laptop. After completing the installation of the utility, you will receive several new components, namely:
- Torrc. This is a configuration file that will be required to make settings for the browser.
- Tor. This is the browser itself, through which you will gain secure access to the network.
- Vidalia. A tool used to set up anonymous surfing.
If you are not familiar with working with a graphical interface, we recommend leaving all settings at their defaults.
Torrent search engine. Pirate city.
Arrr, Johnny was a great guy, we still remember him over the next mug, but meanwhile our ship arrived in the harbor of a famous pirate city, where pirates from all over the world gather. Here we met Little Rat Jack, the Red Beard Baron, and of course the well-known pirates Cynical Deathbringer, and the Red Beast, who, as always, sat by the window in the bar, and I have personal scores with her.
In the last article, I ended with the sad loss of the server due to the DMCA and how poorly the service worked under the torus with all the mirrors, but still worked. From that moment on, I never really set up a stable server that I could brag about as before, and tor2web servers were dying like flies. I don’t even know, apparently dark times have come for the deep web, or general trust and the need for mirrors has waned. Well, maybe it’s for the better, Tor was initially a temporary solution and not very user-friendly.
Now I have some free days, and I decided to think about an alternative search engine option that could be used regardless of the circumstances, and it would not depend on my server or any other. After all, someday they may shut down not only my search engine, but also the root tracker, rutor, as is now happening with many search engines in the West. But this is the most critical part of the torrent infrastructure - the loss of any popular torrent tracker is quite significant. For example, I was a little saddened to learn that not so long ago we lost our valiant captain Nyaa Torrents (well, excuse me, I’m slow and only recently found out about this).
In general, in order to solve some of the problems, I decided to make a separate standalone version of the search engine for the desktop (for now on Windows, I will soon release it for a Mac with a line). In general, this is all the same, only it does not depend on the server and can collect your local torrent database for search. Moreover, you can even exchange databases and add to existing ones. In fact, this is still an early alpha and some things that worked may not work correctly, not to mention a whole pack of bugs that can obviously make it difficult to use on a desktop. Further in the article we will talk about the technical features of using the desktop version. (You can leave bug reports here - https://github.com/DEgITx/rats-/issues)
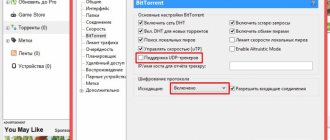
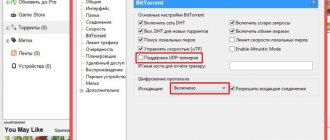
To collect new torrents, make sure that you have 4445 and 4446 open (especially UDP ports!). Expect adequate settings in future versions.
The speed of collecting torrents increases gradually, starting little by little and accelerating. During a day of continuous operation, obtaining statistics can speed up significantly, greatly loading both the network and resources, so the settings provide quotas for the use of the processor and network, but the settings window itself will appear in the next version, such a paradox. There is a mode without collecting torrents, it is in the web version but not in the desktop version and will also be available later.
The torrent database will be located somewhere here:
c:UsersYOUR_USERAppDataRoamingRats on The Boatdatabase
Why am I leaving this path, if the database suddenly becomes damaged, and this sometimes happens with incorrect completion (a known bug), I would not want my clubfoot to become the cause of indignation after 5 days of continuous harvesting (torrents). In general, this is a backup folder of the collected torrent database: close the application either through the tray or through a cross, back up the database. These same databases can be exchanged. In the future, there will most likely be tools for synchronizing them.
Now a little bit of what has changed since the last article. The top current torrents, aka rutor, have appeared - you can see what is currently relevant there. Not very useful, but it might be useful to someone.
Basic filters have appeared that work normally in the web version and are a bit limited in the desktop version:
You can connect the original database from
50,000 torrents, which you can continue to collect further. For obvious reasons, it is not included in the build. I will leave a link to the database in the comments.
Advantages and disadvantages
In this section, we will understand the strengths and weaknesses of the component we discussed today. First, let's highlight the advantages.
Advantages:
- Clear user interface in Russian.
- Nice design.
- Reliable protection and complete anonymity.
- High performance.
- Minimum PC requirements.
- Providing access to sites that have been blocked.
Flaws:
- It is not always possible to connect to the network the first time.
- Only a professional can understand all the functions.
- Updates are not released by the official developer.
It should be noted that if you want to understand the component settings in more detail, for example, how to configure it for UTorrent or download earlier versions (2018-2019), you can use a training video. There is a huge selection of such videos on the Internet.
Does your ISP block access to trackers?
Before switching your torrent client to communicate with trackers via the Tor network, you need to make sure that your provider is preventing you from connecting directly with trackers. Below we will describe several methods that will help you determine whether your ISP is blocking.
ValdikSS/blockcheck
In a nutshell. Download the latest version of the program from https://github.com/ValdikSS/blockcheck/releases and run it in the console. The program's text output will tell you what it found.
Website: https://github.com/ValdikSS/blockcheck.
A utility for determining the type of site blocking from a single register of prohibited information on the provider’s side. This utility allows you to determine:
- Substitution of DNS responses.
- DNS server redirection.
- Blocking DNS servers.
- “Normal” DPI (URL filtering on specific IP addresses and ports).
- “Full” DPI (URL filtering on all IP addresses and/or ports).
- Substitution of an SSL (HTTPS) certificate (listening to HTTPS traffic).
- Blocking by IP address.
The application automatically sends statistics about the type of blocking used to the server. https://habrahabr.ru/post/229377/ - statistics on providers.
Download
Using the button attached in this section, you can download Vidalia via torrent from the official source.
| Program edition: | 2.2.36 |
| Publisher: | Tor Project |
| Year of issue: | 2021 |
| Name: | Vidalia Bridge Bundle |
| Operating system: | Microsoft Windows 32/64 Bit |
| Interface: | Russian |
| License: | For free |
| Archive password: | fraps.pro |
Funny picture
First, let's turn to the style of primitivism and look at the final picture we want to arrive at.
The provider blocks direct connections to trackers via HTTP, but we will bypass them. The torrent client will be given a proxy server running on the local computer, this is Privoxy, the client communicates with it via HTTP, sending distribution statistics to the tracker and receiving lists of participants in this distribution. Privoxy decides that all requests addressed to trackers (that is, bt*.rutracker.cc and bt*.t-ru.org) will be redirected to the Tor client running on the same computer using the SOCKS protocol, and other requests (for example, technical ones from the torrent client; not shown in the figure) will go directly to their addresses. Tor, having received these requests, sends them through its network of several Tor nodes, and as a result they reach the tracker servers. In response to them in the opposite direction, the client receives from the trackers the data necessary for quick work: downloading and searching for distributions.
Communication directly with the peers participating in the distributions is carried out directly, without the Torus network. Also, to detect new peers without the participation of tracker servers in the client, DHT and PEX technologies can be used.
Will changing DNS eliminate problems with torrent blocking?
Not really.
If your provider uses DNS filtering to block access to torrent sites, then you can change the DNS. And your DNS queries will go through a different DNS server than your ISP.
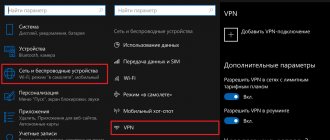
To do this, it is recommended to use the following settings:
- OpenDNS : 208.67.222.222 and 208.67.220.220.
- Google Public DNS : 8.8.8.8 and 8.8.4.4.
- Cloudflare DNS: 1.1.1.1.
However, changing DNS will not prevent the ISP from blocking torrent traffic directly.
Yes, by changing your DNS you can access torrent trackers, but your ISP can use DPI technology to view unencrypted DNS queries even if you are using a third-party DNS server.
The provider can see all requests, for example, to Cloudflare DNS (1.1.1.1), and to any torrent tracker (for example, thepiratebay.org). As a result, the provider rejects all DNS requests, which will lead to connection errors.
It's better to use DNS over HTTPS to encrypt your requests (CactusVPN will help you do this), or use a VPN with encrypted DNS servers. The second option is preferable because it can unblock both torrent trackers and traffic.