I've changed 4 or 5 SIM cards in my entire life. I never suspected what was happening to them. Imagine my surprise when I learned that it turns out that operators are reusing old numbers. And you need to part with the SIM card itself “on good terms” so that no problems arise - this is one of the rules of digital hygiene. You can’t just throw the card in the trash or throw it in a drawer. We tell you how to avoid problems when you change your number.
We tell you why you should be careful about changing your number
What do they do with old phone numbers?
Older SIM cards usually have a feature that automatically switches off and terminates the contract if you don't use it for a certain period of time. For telecom operators, the period varies from 1 to 6 months. You can simply stop using it or stop paying for communications - first the operator will block it and re-issue it. This happens because the number of numbers is limited (and numbers too), so operators are forced to put this number back on sale.
Don't forget to use all the money from your old SIM card
Be sure to spend all the money from your account, otherwise the operator will begin to write it off completely .
The blocking also applies to new cards. If you purchased it, but did not activate it, do not be surprised that after a few months you will not be able to activate the number - it will be blocked.
Why unlink your phone from your account?
In 2021, changing your number is equivalent to changing your place of residence, if not worse. Just imagine how many different accounts are linked to your SIM card, you can’t remember them all: social networks, online stores, banks... It is believed that more than 60% of numbers, even after reissue, are still linked to accounts of different services.
Don't forget to change phone numbers on important accounts
First of all, take care to unlink accounts from it; in case of loss or theft of data, operators are not responsible for the disclosure of data and do not protect it. If you start to experience problems using a card with a new number (SMS, calls are received), then you should contact your operator about this problem.
Dimensions too large
The compact size of SIM cards that are relevant today is almost their main feature, which immediately catches the eye. Compared to Mini format modules (25 x 15 x 0.76 mm), their younger brothers Micro (15 x 12 x 0.76 mm) and Nano (12.3 x 8.8 x 0.67 mm) occupy quite a small space space in the smartphone case.
All the details about the types and sizes of SIM cards are in this article.
That is why almost every mobile device developer creates smartphones for new types of SIM cards. Today it is unlikely that you will be able to find a current device that supports the old Mini format.
Why notify about a number change?
If you changed your number but did not notify your friends, the calls will be sent to the new owner. Often, such numbers end up in the hands of scammers who use the information for personal gain: they can find out your address, personal data, and the possibility of using this information to hack social networks or an online banking account.
Notifying your friends about a number change is quite simple and useful.
Be sure to inform your friends and loved ones about the change of number, preferably in a personal conversation. Experts recommend not using personal numbers when selling goods and on the Internet - for such operations it is better to get another SIM card. How often do you change your number? Tell us about your experience in our Telegram chat.
Protected SIM card (thermal SIM card)
Special SIM card of increased strength and wear resistance. The protected SIM card is made of special moisture- and heat-resistant plastic that can withstand temperatures of −40 to +105 °C while maintaining functionality, and the contact group is coated with a special varnish that prevents corrosion and reduces the physical and chemical effects on the metal contacts. Also, cards of this type have an increased service life - for 13 years at a temperature of 25 ° C, the recorded data is guaranteed to remain intact.
As a rule, such high-tech development is rarely used by individuals: it was originally intended for machine-to-machine communication and use in special devices, such as GPS/GLONASS trackers or security systems. A protected SIM card can be useful for subscribers living in harsh weather conditions of the North or southern regions and specialists whose work involves exposure to aggressive environments, temperature changes, vibration and other conditions of increased danger.
How to hack a social media account from an old number
Many social networks require a phone number to be linked to your account, and instant messengers cannot be used without it. This is a great way to save your data, because two-factor authentication codes are sent to your phone. On social networks, it is still not difficult to go to someone’s page using an old number, and then send out the famous “request for help” to your friends.
Two-factor authentication helps, but the verification code may come to the old number
Don’t forget to unlink your old number from messengers to avoid problems: just enter your phone number in the messenger search to find out a lot of new things. Try to turn off the display of the real number, leave a nickname.
How to steal money from an account
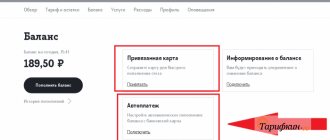
After changing your number, do not forget to go to the bank application. Losing social networks is not as scary as being left without honestly earned ones. Stealing money is the most important goal of scammers. Access to bank applications provides ample opportunities for life (albeit your own) - from using your card to applying for a loan.
Online banks are the main place to change your number
Don’t forget about marketplace applications - changing your old number to a new one is just as mandatory there as in online banking. To avoid ending up broke, try not to leave linked maps in your apps. Better yet, use virtual cards that won’t let you get ripped off completely. Find even more information about Internet safety in our Yandex.Zen.
Self-cutting SIM cards
Let's assume you don't have the opportunity to visit a phone shop, but you need to use the phone. In such a situation, try to cut the SIM card yourself. The new cards already have the required dimensions marked on a plastic base, so it is convenient to take them out from there by simply cutting off the places where the staples are located with a knife. The situation is worse if the SIM card is a very old model.
These cards have a chip that no longer fits into the Nano's dimensions (70% of smartphones have such slots). So you can only cut it to Micro. There is a sample millimeter on the Internet.
- Mark the card with a pen where you want to cut it. It’s better if you already have another microSIM and you simply circle it and place it on top.
- Carefully cut out the plastic according to the drawing, preferably with nail scissors or a thin blade.
- Do not touch the chip - the slightest scratch on it and the SIM card will stop working.
What to do if State Services are hacked
Not everyone loves this application, but every year it gets better, while simultaneously absorbing our data: from document numbers to fines. Why would anyone know about this? If you got rid of your SIM card, replace the number in this important application. Having a separate number assigned to someone close to you is a great idea - it can be used for important things that need to be protected from prying eyes. This will confuse the scammers and save you from problems.
Losing access to public services is tantamount to losing your passport
Changing your number is not a reason to neglect your old SIM card. You need to unlink numbers from different services and pages, remind your friends that you now have different contacts. Previously, changing your number was not as problematic as it is now - it’s convenient that there is a function to switch to another operator, which helps save time and nerves.
How SIM cards work. Part one: history of the issue
The familiar SIM card, which is so easy to move from one phone to another, did not appear at all simultaneously with the birth of the mobile phone as such. The first mobile phones worked in “tethered” communication standards: subscription parameters were written directly into the memory of the mobile terminal. Moreover, in the oldest analog standards like NMT-450 - even without protection: if desired, you could copy the recording to another telephone set and create a clone of it, talk at the expense of the owner or receive calls addressed to him.
A little later, a security solution appeared - the so-called SIS code: an 18-digit number, unique for each device and hardwired into a special processor. SIS codes were distributed centrally between manufacturers, so there could not be two devices with the same code. The same processor also stored a seven-digit RID code, which was transmitted to the base station when registering on the network.
Treasure SIM card: how to lose everything by losing just your phone - https://t.co/ElKB4U1unJ
— Kaspersky Lab (@Kaspersky_ru) November 17, 2014
From there, a randomly generated number came in return, and the SIS processor, based on this number and its unique SIS response, had to generate a key, based on the correctness of which authorization took place.
The short length of both the keys and the generated numbers was quite sufficient in those days (we are talking about 1994), although the system was later hacked. However, three years earlier, the GSM digital standard appeared, in which a similar, but more robust authorization system was initially implemented, and the standard itself became “untethered”.
5G cellular networks: how they will work, why they are needed and when they will be available - https://t.co/27iaXMktJE pic.twitter.com/wnkjiuaos9
— Kaspersky Lab (@Kaspersky_ru) May 22, 2015
That is, the authorization functions were assigned not to the device itself, but to an external processor built into a smart card, which was called SIM (Subscriber Identity Module). Subscriber subscription data is no longer dependent on the device itself - it has become possible to use any device, changing them as often as desired.
A SIM card is essentially an ISO 7816 smart card and is not particularly different from other contact chip cards - for example, bank or payphone cards. The first “SIM cards” had exactly the same size, which is what telecom operators’ starter packages still remind us of today: simply the miniaturization of phones very quickly led to the fact that full-size cards (1FF) no longer fit inside the devices, so they came up with an easily breakable module (mini-SIM or 2FF), which contains the chip and pads, but much less unnecessary plastic.
Despite further miniaturization (micro-SIM - 3FF, and then nano-SIM - 4FF), the shape and location of the contact pads, as well as the principles of operation of the built-in chips have remained unchanged for almost 25 years, and large plastic “blanks” are still are issued so that even a subscriber with a very old phone can use the services - this is the standard.
Typically, many older devices will not be able to read a modern SIM card, even if it is full-size. The fact is that previously, a voltage of 5 V was used everywhere to power the processor of a SIM card, but now 3 V is used. And for the sake of economy, many manufacturers produce SIM cards that support only one voltage, and not two - in an old five-volt cell phone SIM card power protection will simply work and the processor will not work.
A modern smartphone is a full-fledged computer. A very dangerous computer. Let's tell you why https://t.co/2uibZkeLc6 pic.twitter.com/ILw4G8eQHl
— Kaspersky Lab (@Kaspersky_ru) November 15, 2015
Already at the production stage, the IMSI (International Mobile Subscriber Identity) for the specific operator ordering the module, as well as the 128-bit Ki key (Key Identification, “individual user authentication key”) are recorded in the permanent memory of the SIM card already at the production stage. . To put it roughly, this is the subscriber’s login and password, tightly hardwired into the hardware of the SIM card.
The correspondence between the IMSI of a specific subscriber's account and his telephone number is stored in the operator's database called HLR (Home Location Register, “subscriber information database”). This data is copied into a temporary VLR (Visitor Location Register) database in each specific network segment in which the subscriber is located at a certain point in time.
2 billion compromised #Gemalto SIM cards - a nightmare or nonsense? https://t.co/9gRdY9Sb0Z pic.twitter.com/IdnjjrwRwn
— Kaspersky Lab (@Kaspersky_ru) March 10, 2015
Authorization is very simple: upon registration, the VLR sends a 128-bit random number (RAND) to the subscriber’s phone, from which, based on the Ki key, the SIM card processor calculates a 32-bit SRES response using the A3 algorithm, which is sent back to the VLR. If the answer matches the expected one, then registration occurs on the network.
According to another algorithm, A8, also based on RAND and Ki, another temporary key is calculated - Kc. And based on this key, the third algorithm, A5, encrypts the data transmitted over the air.
By default, encryption is always enabled, but in some cases (for example, at the request of the FSB during special operations) it can be turned off - then conversations take place without encryption and are easily intercepted from the air. On old phones, at this moment an open lock is displayed on the display; on modern smartphones, except BlackBerry, there is complete silence about this.
Is it easy to hack a cellular network? I would like to believe that it is difficult, but in reality... https://t.co/9sS01xS55j pic.twitter.com/aXIznfpXNL
— Kaspersky Lab (@Kaspersky_ru) November 23, 2015
By the way, there is an attack for listening to telephone conversations over the air - using a device called IMSI Catcher. It emulates the base station where phones are registered and relays all signals to a real BS.
In this case, the entire authorization process occurs as usual (key hacking is not required), but the “fake” base station gives the device a command to work without encryption, accordingly, the call without encryption passes through it and is listened to without the knowledge of the operator.
It is interesting that such a vulnerability is not a “bug” of the standard at all, but the very “feature” incorporated at the development stage at the request of the intelligence services so that they could implement Man-In-The-Middle attacks during operational investigations. events.