Now mobile Internet is relatively inexpensive, but this is not a reason to throw it away left and right. Full unlimited service still costs a pretty penny, and many operators, by the way, are already giving up such luxury.
Most of the available tariffs are conditionally unlimited, that is, they provide a certain and rather limited amount of traffic per day or month. If you exceed the limit, the speed will drop to the level of a dial-up modem and it will become impossible to use the Internet.
Perhaps you do not fit into the volume provided under the tariff or are dangerously close to the limit. Perhaps you want to save some traffic reserve so that you can use it when urgently needed. In any case, it is useful to be able to save megabytes, and now we will tell you how to do this.
Get rid of pest apps
Increased traffic consumption is not always related to your appetite. Often the unjustified gluttony of individual applications is to blame. Such scoundrels sit in the background and constantly transmit and send something. You can find them using a standard tool that is built into any current version of Android.
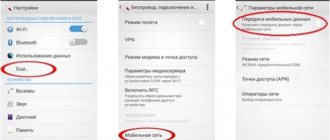
- Go to Android settings.
- Select Data Transfer.
- Select Mobile Data Transfer.
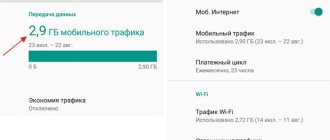
Here you will see a general graph of mobile traffic consumption, and below it - a rating of the most voracious residents of the system.
To curb the ardor of an individual application, tap on it and turn off the background mode. After this, the sly one will not be able to receive and send data in the background.
The problem is that in order to identify scoundrels, you need to understand what the normal Internet consumption is for a particular application. Obviously, the browser, music and video streaming services, as well as maps are capable of eating hundreds of megabytes, but offline-oriented and working with a small amount of data have nothing on this list.
Traffic extension
The traffic on the phone has ended, the modem is silent, the tablet is inactive - the situation is not pleasant, especially since there is still a lot of time until the end of next month. Let's look at how to increase the amount of traffic on a particular operator.
Extension of traffic from MTS
This operator offers subscribers many so-called “Turbo buttons”. An additional 100 MB will cost 30 rubles, 500 MB – 95 rubles, 1 GB – 175 rubles, 2 GB – 300 rubles, 5 GB – 450 rubles, 20 GB – 900 rubles. Unlimited for 3 hours costs 95 rubles, for 6 hours – 150 rubles. To order additional packages, visit the resource https://i.mts.ru/ or use the mobile application - you can get confused with USSD commands.
Extension of traffic from MegaFon
Here are additional options for subscribers to choose from:
- “Extend Internet 1 GB” – 1 GB of Internet traffic for 175 rubles;
- “Extend Internet 5 GB” – 5 GB of Internet traffic for 400 rubles;
- “Extend Internet XS” – 70 MB for 19 rubles (valid for a smartphone or tablet).
The set is quite modest, but nothing can be done.
Extending traffic on Beeline
Provided here. It will add 5 GB for 150 rubles in automatic mode, if it has not been disabled previously. There is nothing else interesting and useful on Beeline.
Extension of traffic on Tele2
The options for the “Internet for Devices” tariff provide additional packages - up to five pieces of 1 GB each. The cost of one package is 100 rubles. Once they are exhausted, Internet access is suspended completely. It turns out insanely expensive and completely uninteresting.
Extending traffic on Yota
For tablet PCs and modems/routers, unlimited is offered here, so there is nothing special to renew. On phone plans, traffic is limited. Here you can order additional packages of 5 GB for 100 rubles each - their number is not limited in any way.
5/5 — (2 votes)
Set up a warning and traffic limit
- Go to Android settings.
- Select Data Transfer.
- Select "Payment Cycle".
The billing cycle is the date when the subscription fee is charged. Usually a new Internet package is given on the same day. Specify it so that the system knows the date the traffic counter was reset.
- Enable "Alert Settings".
- Select Alerts.
- Specify the amount of traffic upon reaching which the system will notify you about it.
If you want to strictly limit traffic consumption, enable “Set traffic limit” and specify the value, upon reaching which the system will turn off the mobile Internet.
How traffic is spent
The user pays for a specific dedicated package, which includes minutes of calls and access to the global network. When used and connected to the global network, the phone constantly sends requests and receives responses in the form of data. All data has a certain weight, which is calculated in megabytes or gigabytes. Well, as you already understood, in this situation, the amount of Internet used is limited, and when the package reaches zero, access is disabled.
Further, many operators make it possible to purchase additional gigabytes for a dedicated fee.
Enable data saving in individual applications
Any normal developer, if his application works with potentially large amounts of data, can optimize traffic consumption using settings. For example, almost all Google tools can save precious megabytes of mobile Internet.
Google Chrome
- Go to Google Chrome settings.
- Select Data Saver.
- Turn on the “Traffic Saving” mode.
In addition to Google Chrome, a traffic saving mode is provided in the Opera browser.
Opera browser: fast and private
Opera
Price: Free
Download
Price: Free
YouTube
- Go to YouTube settings.
- Select General.
- Turn on the “Traffic Saving” mode.
Google Maps
- Go to Google Maps settings.
- Turn on “Wi-Fi only” and follow the “Your offline maps” link.
Offline maps allow you to save hundreds of megabytes of traffic. Be sure to download the area where you live and don’t forget to add areas you plan to visit in the near future.
- Click Other Area.
- Use pan and zoom gestures to select the area to download and click "Download".
- Click on the gear icon in the upper right corner of the Downloaded Areas menu.
- Select "Download Settings" and select "Wi-Fi Only".
Google Press
- Go to Google Press settings.
- Select Data Saver Mode and select On.
- In the "Download" section, turn on the "Wi-Fi only" mode.
Google Photos
- Go to Google Photos settings.
- Select "Startup and Sync".
- Find the “Use mobile internet” section and disable the option for photos and videos.
Google Music
- Go to your Google Music settings.
- In the Playback section, lower the quality when streaming over a mobile network.
- In the “Downloading” section, allow downloading music only over Wi-Fi.
If necessary, allow music playback only over Wi-Fi.
Google Music can save albums for offline listening. You can download music to your device if you have Wi-Fi and play it without an Internet connection.
- Go to the artist's album list.
- Click on the vertical ellipsis icon in the lower right corner of the album and select “Download” from the menu that appears.
Google Movies
- Go to Google Movies settings.
- Under Mobile Network Streaming, turn on Show Warning and Limit Quality.
- In the Downloads section, select Network and select Wi-Fi only.
How to view traffic on Android
In order to see traffic consumption on an Android mobile phone, you need to open the “ Settings ” application and find the “ Data transfer ” or “ Data usage ” section there. For example, on pure Android 8.0, to do this, you first need to go to the “ Network and Internet ” section, and then open the “ Data Transfer ” subsection.
Here you can see how much traffic was used over the last month and take advantage of the functions that allow you to manage your mobile Internet expenses. There is also information about the amount of information that was transferred via Wi-Fi.
If the information that Android provides is not enough for you, then you can install special applications for traffic counting. For example, you can use the My Data Manager or Traffic Monitor applications.
Types of traffic
Traffic can be viewed from the point of view of an ordinary Internet user and from the point of view of a web analyst.
For the user
Traffic on the Internet is divided into two types: outgoing and incoming.
- Outgoing data. Information that a computer uploads to the Internet. This is what you send to other people: messages on social networks, photos, documents.
- Incoming data. Information obtained from the Internet.
The computer constantly receives and transmits information, so when working on the Internet, both types of traffic are consumed simultaneously.
Sometimes the computer sends information without the user's knowledge. This happens due to viruses that increase outgoing traffic. Check your computer for viruses to avoid losing personal information. Previously, there was a division into internal and external traffic.
- Internal traffic is information transmitted over a local network. The provider does not charge a fee.
- External traffic is information coming from the Internet to a computer or uploaded to the Internet.
Now such a division is outdated: technology has improved and the boundary between internal and external traffic has blurred.
Another type of traffic classification is the division into mobile and desktop traffic. The difference between these two types is the device that is used to access the Internet.
- Mobile traffic is used on phones and tablets. Its speed is limited, information loads slower than on computers. The provider offers a limited traffic package for a month. After the free traffic expires, the provider significantly reduces the speed. You can purchase more megabytes for an additional fee. There are packages that provide high speed and unlimited data during fixed hours of the day, for example, at night. Mobile Internet traffic is gaining popularity. According to Cisco research, global mobile Internet traffic grew by 63% in 2021.
- Desktop or stationary traffic is used on computers. Providers limit the speed, not the amount of information, but nevertheless, Internet speeds on computers are usually faster than on phones.
For web analyst
A web analyst is a person who analyzes resource traffic and promotion effectiveness. For him, Internet traffic is the flow of visitors to the site. =
In this case, traffic can be divided into groups according to the type of site audience:
- Target. The flow of visitors interested in the content of your site. These could be purposeful buyers, students, and so on.
- Non-target. A flow of visitors who are not interested in the site’s content. For example, a random visitor.
By type of traffic source - where the user came to the site from.
- Purchased Traffic or Advertising – Visitors come to your site through paid ads or sponsored links.
- Direct traffic - visitors who like your site and visit it regularly.
- Referral traffic includes referrals from other sites.
- Traffic from social networks is people who came to the site through links posted on social networks.
- Search traffic is visitors who came to your site through a request on search networks.
Activation of the “Automatic speed extension” service
For many subscribers, the Internet is an important component of the mobile service. In order not to be left without access to the Network, experts in this matter advise turning on “auto-renewal speed”. Activating the option will make it possible to avoid problems with speed and not waste time sending various requests or making necessary calls.
The price for the service provided is 20 rubles for 70 MB of traffic, and the package itself is activated automatically, immediately upon completion of the main volume. To activate the service you need:
- send a request to “*115*23#”;
- call 067471778.
These methods are offered only to users of the capital region. If you want to cancel the service, just send a request - “*115*230#” or call 0674717780. Deactivation occurs instantly.
You can extend your traffic here!
Internet traffic - what is it?
When using a desktop computer, the traffic flow is greater than when viewing Internet portals from mobile devices.
Traffic for websites is the number of visitors who visited the resource during a period of time: a day, a month. Let the website be a store and its visitors be the customers. It is important for the store to ensure an influx of new and regular customers and to disseminate information about the selection and quality of the assortment. The situation is similar with websites; traffic expands the capabilities of the resource and brings profit for further development.
Connecting the “Extend Speed” option
The plug-in package allows you to start using the Internet again on convenient terms, but the contents of the package may vary. The main difference is the cost and scope of services provided. Today, all Beeline subscribers have access to different variations of the service. We are talking about the following possibilities:
“Extend Speed – 1 GB”
- USSD “*115*121#”;
- call 0674093221.
- 250 rubles, which are debited from the phone balance after activation of the option.
“Extend Speed – 4 GB”
- USSD “*115*22#”;
- call 0674093222.
- 500 rubles, which are withdrawn from the balance after activation of the service.
Internet access appears and speed is restored immediately after money is withdrawn. The speed when using the Internet can be 236 Kbps – 75 Mbps. An additional option is to activate the Highway package. The service is provided monthly and all you need to do is select a suitable traffic package and have the required amount on your phone balance to activate it. High-speed Internet is not available abroad.
What does traffic on your phone mean?
Traffic refers to the amount of data a smartphone sends to and from the network. This parameter is measured in various units - bits, packets, bytes. Smartphones usually use bytes. By estimating bytes, the user can keep their spending under control.
It is important to consider that traffic is divided into a number of types. These include incoming and outgoing. It can also be external and internal. However, on the phone, as a rule, such detailed statistics regarding traffic usage are not available.
Instead, it shows the total amount of traffic that was used over a certain time. If you need to obtain more accurate values, it is permissible to use special programs. These include, in particular, NetWorx, TMeter, BWMeter, DU Meter.
Principles of organizing IP traffic accounting
Any administrator sooner or later receives instructions from management: “count who goes online and how much they download.” For providers, it is complemented by the tasks of “letting whoever needs it in, taking payment, limiting access.” What to count? How? Where? There is a lot of fragmentary information, it is not structured. We will save the novice admin from tedious searches by providing him with general knowledge and useful links to hardware. In this article I will try to describe the principles of organizing the collection, accounting and control of traffic on the network. We will look at the issue and list possible ways to retrieve information from network devices. This is the first theoretical article in a series of articles devoted to the collection, accounting, management and billing of traffic and IT resources.
Internet access structure
In general, the network access structure looks like this:
- External resources - the Internet, with all sites, servers, addresses and other things that do not belong to the network that you control.
- Access device – router (hardware or PC-based), switch, VPN server or concentrator.
- Internal resources are a set of computers, subnets, subscribers whose operation on the network must be taken into account or controlled.
- A management or accounting server is a device on which specialized software runs. Can be functionally combined with a software router.
In this structure, network traffic passes from external resources to internal ones, and back, through the access device. It transmits traffic information to the management server. The control server processes this information, stores it in the database, displays it, and issues blocking commands. However, not all combinations of access devices (methods) and collection and control methods are compatible. The various options will be discussed below.
Network traffic
First, you need to define what is meant by “network traffic” and what useful statistical information can be extracted from the stream of user data. The dominant internetworking protocol is still IP version 4. The IP protocol corresponds to layer 3 of the OSI model (L3). Information (data) between the sender and the recipient is packaged into packets - having a header and a “payload”. The header determines where the packet is coming from and to (sender and recipient IP addresses), packet size, and payload type. The bulk of network traffic consists of packets with UDP and TCP payloads - these are Layer 4 (L4) protocols. In addition to addresses, the header of these two protocols contains port numbers, which determine the type of service (application) transmitting data.
To transmit an IP packet over wires (or radio), network devices are forced to “wrap” (encapsulate) it in a Layer 2 (L2) protocol packet. The most common protocol of this type is Ethernet. The actual transmission “to the wire” occurs at the 1st level. Typically, the access device (router) does not analyze packet headers at levels higher than level 4 (with the exception of intelligent firewalls). Information from the fields of addresses, ports, protocols and length counters from the L3 and L4 headers of data packets constitutes the “raw material” that is used in traffic accounting and management. The actual amount of information transmitted is found in the Length field of the IP header (including the length of the header itself). By the way, due to packet fragmentation due to the MTU mechanism, the total volume of transmitted data is always greater than the payload size.
The total length of the IP and TCP/UDP fields of the packet that are interesting to us in this context is 2...10% of the total length of the packet. If you process and store all this information batch by batch, there will not be enough resources. Fortunately, the vast majority of traffic is structured to consist of a series of “conversations” between external and internal network devices, called “flows.” For example, as part of one operation of sending an email (SMTP protocol), a TCP session is opened between the client and the server. It is characterized by a constant set of parameters {source IP address, source TCP port, destination IP address, destination TCP port}
. Instead of processing and storing information packet by packet, it is much more convenient to store flow parameters (addresses and ports), as well as additional information - the number and sum of lengths of packets transmitted in each direction, optionally session duration, router interface indexes, ToS field value, etc. This approach is beneficial for connection-oriented protocols (TCP), where it is possible to explicitly intercept the termination of a session. However, even for non-session-oriented protocols, it is possible to perform aggregation and logical completion of a flow record based on, for example, a timeout. Below is an excerpt from the SQL database of our own billing system, which logs information about traffic flows:
It is necessary to note the case when the access device performs address translation (NAT, masquerading) to organize Internet access for local network computers using one, external, public IP address. In this case, a special mechanism replaces IP addresses and TCP/UDP ports of traffic packets, replacing internal (not routable on the Internet) addresses according to its dynamic translation table. In this configuration, it is necessary to remember that in order to correctly record data on internal network hosts, statistics must be collected in a way and in a place where the translation result does not yet “anonymize” internal addresses.
Methods for collecting traffic/statistics information
You can capture and process information about passing traffic directly on the access device itself (PC router, VPN server), transferring it from this device to a separate server (NetFlow, SNMP), or “from the wire” (tap, SPAN). Let's look at all the options in order.
PC router
Let's consider the simplest case - an access device (router) based on a PC running Linux.
Much has been written about how to set up such a server, address translation and routing. We are interested in the next logical step - information on how to obtain information about the traffic passing through such a server. There are three common methods:
- intercepting (copying) packets passing through the server’s network card using the libpcap library
- intercepting packets passing through the built-in firewall
- using third-party tools for converting packet-by-packet statistics (obtained by one of the two previous methods) into a netflow aggregated information stream
Libpcap
In the first case, a copy of the packet passing through the interface, after passing the filter (man pcap-filter), can be requested by a client program on the server written using this library.
The packet arrives with a layer 2 header (Ethernet). It is possible to limit the length of the information captured (if we are only interested in information from its header). Examples of such programs include tcpdump and Wireshark. There is an implementation of libpcap for Windows. If address translation is used on a PC router, such interception can only be carried out on its internal interface connected to local users. On the external interface, after translation, IP packets do not contain information about the internal hosts of the network. However, with this method it is impossible to take into account the traffic generated by the server itself on the Internet (which is important if it runs a web or email service). libpcap requires support from the operating system, which currently amounts to installing a single library. In this case, the application (user) program that collects packages must:
- open the required interface
- specify the filter through which to pass received packets, the size of the captured part (snaplen), the buffer size,
- set the promisc parameter, which puts the network interface into capture mode for all packets passing by, and not just those addressed to the MAC address of this interface
- set a function (callback) called on each received packet.
When a packet is transmitted through the selected interface, after passing the filter, this function receives a buffer containing Ethernet, (VLAN), IP, etc. headers, total size up to snaplen. Since the libcap library copies packets, it cannot be used to block their passage. In this case, the traffic collection and processing program will have to use alternative methods, such as calling a script to place a given IP address in a traffic blocking rule.
Firewall
Capturing data passing through the firewall allows you to take into account both the traffic of the server itself and the traffic of network users, even when address translation is running. The main thing in this case is to correctly formulate the capture rule and put it in the right place. This rule activates the transfer of the packet towards the system library, from where the traffic accounting and management application can receive it. For Linux OS, iptables is used as a firewall, and interception tools are ipq, netfliter_queue or ulog. For OC FreeBSD – ipfw with rules like tee or divert. In any case, the firewall mechanism is complemented by the ability to work with a user program in the following way:
- A user program - a traffic handler registers itself in the system using a system call or library.
- A user program or external script installs a rule in the firewall, “wrapping” the selected traffic (according to the rule) inside the handler.
- For each passing packet, the handler receives its contents in the form of a memory buffer (with IP headers, etc. After processing (accounting), the program must also tell the operating system kernel what to do next with such a packet - discard it or pass it on. Alternatively, it is possible pass the modified packet to the kernel.
Since the IP packet is not copied, but sent to the software for analysis, it becomes possible to “eject” it, and therefore, completely or partially restrict traffic of a certain type (for example, to a selected local network subscriber). However, if the application program stops responding to the kernel about its decision (hung, for example), traffic through the server is simply blocked. It should be noted that the described mechanisms, with significant volumes of transmitted traffic, create excessive load on the server, which is associated with the constant copying of data from the kernel to the user program. The method of collecting statistics at the OS kernel level, with the output of aggregated statistics to the application program via the NetFlow protocol, does not have this drawback.
Netflow
This protocol was developed by Cisco Systems to export traffic information from routers for the purpose of traffic accounting and analysis. The most popular version 5 now provides the recipient with a stream of structured data in the form of UDP packets containing information about past traffic in the form of so-called flow records:
The amount of information about traffic is several orders of magnitude smaller than the traffic itself, which is especially important in large and distributed networks. Of course, it is impossible to block the transfer of information when collecting statistics via netflow (unless additional mechanisms are used). Currently, a further development of this protocol is becoming popular - version 9, based on the template flow record structure, implementation for devices from other manufacturers (sFlow). Recently, the IPFIX standard was adopted, which allows statistics to be transmitted via protocols at deeper levels (for example, by application type). The implementation of netflow sources (agents, probes) is available for PC routers, both in the form of utilities working according to the mechanisms described above (flowprobe, fprobe, softflowd), and directly built into the OS kernel (FreeBSD: ng_netgraph, Linux: ipt_neflow). For software routers, the netflow statistics stream can be received and processed locally on the router itself, or sent over the network (transfer protocol - over UDP) to the receiving device (collector).
A collector program can collect information from many sources at once, being able to distinguish their traffic even with overlapping address spaces. Using additional tools such as nprobe, it is also possible to perform additional data aggregation, stream bifurcation or protocol conversion, which is important when managing a large and distributed network with dozens of routers.
Netflow export functions support routers from Cisco Systems, Mikrotik, and some others. Similar functionality (with other export protocols) is supported by all major network equipment manufacturers.
Libpcap “outside”
Let's complicate the task a little. What if your access device is a hardware router from another manufacturer? For example, D-Link, ASUS, Trendnet, etc. It is most likely impossible to install additional data acquisition software on it. Alternatively, you have a smart access device, but it is not possible to configure it (you don’t have rights, or it is controlled by your provider). In this case, you can collect information about traffic directly at the point where the access device meets the internal network, using “hardware” packet copying tools. In this case, you will definitely need a separate server with a dedicated network card to receive copies of Ethernet packets. The server must use the packet collection mechanism using the libpcap method described above, and our task is to submit a data stream identical to that coming from the access server to the input of the network card dedicated for this. For this you can use:
- Ethernet - hub: a device that simply forwards packets between all its ports indiscriminately. In modern realities, it can be found somewhere in a dusty warehouse, and using this method is not recommended: unreliable, low speed (there are no hubs with a speed of 1 Gbit/s)
- Ethernet – a switch with the ability to mirror (mirroring, SPAN ports. Modern smart (and expensive) switches allow you to copy all traffic (incoming, outgoing, both) of another physical interface, VLAN, including remote (RSPAN) to a specified port
- A hardware splitter, which may require the installation of two network cards instead of one to collect - and this is in addition to the main, system one.
Naturally, you can configure a SPAN port on the access device itself (router), if it allows it - Cisco Catalyst 6500, Cisco ASA. Here is an example of such a configuration for a Cisco switch: monitor session 1 source vlan 100! where do we get the packets monitor session 1 destination interface Gi6/3! where do we issue packages?
SNMP
What if we don’t have a router under our control, we don’t want to contact netflow, we’re not interested in the details of our users’ traffic. They are simply connected to the network through a managed switch, and we just need to roughly estimate the amount of traffic going to each of its ports. As you know, network devices with remote control support and can display counters of packets (bytes) passing through network interfaces. To poll them, it would be correct to use the standardized SNMP remote management protocol. Using it, you can quite easily obtain not only the values of the specified counters, but also other parameters, such as the name and description of the interface, MAC addresses visible through it, and other useful information. This is done both by command line utilities (snmpwalk), graphical SNMP browsers, and more complex network monitoring programs (rrdtools, cacti, zabbix, whats up gold, etc.). However, this method has two significant drawbacks:
- Traffic blocking can only be done by completely disabling the interface, using the same SNMP
- traffic counters taken via SNMP refer to the sum of the lengths of Ethernet packets (unicast, broadcast and multicast separately), while the rest of the previously described tools give values relative to IP packets. This creates a noticeable discrepancy (especially on short packets) due to the overhead caused by the length of the Ethernet header (however, this can be approximately combated: L3_byte = L2_byte - L2_packets * 38).
VPN
Separately, it is worth considering the case of user access to the network by explicitly establishing a connection to the access server. A classic example is the good old dial-up, the analogue of which in the modern world is VPN remote access services (PPTP, PPPoE, L2TP, OpenVPN, IPSEC)
The access device not only routes user IP traffic, but also acts as a specialized VPN server and terminates logical tunnels (often encrypted) within which user traffic is transmitted. To account for such traffic, you can use all the tools described above (and they are well suited for deep analysis by ports/protocols), as well as additional mechanisms that provide VPN access control tools. First of all, we will talk about the RADIUS protocol. His work is a rather complex topic. We will briefly mention that the control (authorization) of access to the VPN server (RADIUS client) is controlled by a special application (RADIUS server), which has a database (text file, SQL, Active Directory) of allowed users with their attributes (restrictions on connection speeds, assigned IP addresses). In addition to the authorization process, the client periodically transmits accounting messages to the server, information about the state of each currently running VPN session, including counters of transmitted bytes and packets.
Conclusion
Let's bring all the methods for collecting traffic information described above together:
Let's summarize. In practice, there are a large number of methods for connecting the network you manage (with clients or office subscribers) to an external network infrastructure, using a number of access tools - software and hardware routers, switches, VPN servers. However, in almost any case, it is possible to come up with a scheme where information about traffic transmitted over the network can be sent to a software or hardware tool for its analysis and management. It is also possible that this tool will allow feedback to the access device, using intelligent access restriction algorithms for individual clients, protocols, and other things. This is where I will finish the analysis of the materiel. The remaining unanswered topics are:
- how and where the collected traffic data goes
- traffic accounting software
- What is the difference between billing and a simple “counter”
- How can you impose traffic restrictions?
- accounting and restriction of visited websites
How to save traffic
There are a huge number of background applications on the phone that constantly use extra gigabytes. The best way is to constantly turn off your mobile Internet when you don’t need it. You can also try turning off these programs and removing widgets with weather and exchange rates. I can’t say exactly how to do this, since all phones have different firmware.
In the section where the number of gigabytes in use is located, you can also see a list of programs that actively use the Internet. Some of them can be removed or turned off.
If possible, connect and use Wi-Fi networks. In the settings of some browsers there is a “Traffic Savings” add-on.
Go through all installed programs and remove unnecessary and redundant ones. Also in some applications in the settings there is an option to use the Internet only when connected to WiFi - but this add-on must be enabled separately. And the best option is not to worry and connect to an unlimited package, if possible.
Programs for compressing and monitoring mobile traffic
These programs allow you to find out which application is using the Internet, if you need to deny access to selected applications, and compress the rest of the traffic by passing it through a VPN. We warn you that the programs described below can reduce the speed, so you can try to make your mobile Internet faster using our instructions. All you have to do is choose one of the three programs presented below, install it and configure it to suit your needs - fortunately, the programs are quite simple and two of them are entirely in Russian.
Check where your traffic is going
Anyone whose Internet speed drops dramatically after two weeks of use either has an unprofitable data plan or several hidden data consumers on their smartphone. To save your traffic, you need to first check that none of the apps are using data without your knowledge.
On iOS
you can do this in the "Settings" of the mobile network. If among them there are applications that you do not use, but which consume mobile traffic, then disable them.
Android users
can check the Data Consumption or Data Usage menu in Settings. Set thresholds for first warning or stopping data usage completely.
How to find out the remaining traffic on a Beeline modem and router?
To find out the available remaining traffic on the USB modem, go to the modem settings menu, select the “Statistics” tab. You will see how many megabytes are received after connecting the package. You can also send a short command *102# from the modem. The information will be sent via SMS message.
To find out the rest of your home Internet package, go to your Personal Account on the website beeline.ru. log in and go to the “Details” section, then “Internet traffic”. Here you will see the number of megabytes transmitted and received, the cost of services for the period of interest, the balance and the date when you need to make the payment.
Use the “Traffic Saving” mode on Android
To activate data saving on your Android smartphone, follow these steps.
- Open Android settings.
- In the window that opens, select “Data transfer”.
- Activate the “Traffic Saving” mode.
If you figured out how to enable data saving on Android and did everything correctly, then after activating this mode, the system will automatically turn off background data sending for most installed applications. This will lead to a significant reduction in overall Internet consumption. If you want to disable traffic saving mode on Android for individual applications, just click on the appropriate item.
How to get mobile traffic information
The difference between regular and mobile traffic is the amount of packet data consumed. On smartphones, the Internet is consumed in less quantity, due to the adaptation of sites to a compressed mobile version.
There are three ways to determine mobile traffic:
- downloading software from the telecom operator;
- sending a short number to receive information;
- viewing the statistics section in your phone settings;
By installing a special application from your telecom operator, you can find out how much mobile Internet has been spent. To receive quick information, you can also use short USSD numbers.
Information about the Internet resource spent on the phone is stored in the “statistics” section. For example, the path in an Android smartphone with the Megafon operator looks like this: “Settings > Data transfer > MEGAFON.”